In a society where security is becoming increasingly critical daily, one thing is clear: traditional passwords are no longer adequate. Whether it is for online banking, social networks, or email, a password is crucial. As such, an essential part of one’s digital lifestyle becomes the remembering of multiple complex passwords and the fear of them being disloyal and unreliable; downright tiresome. That’s why biometrics come into play as an advanced, more reliable yet convenient alternative that claims to change the way people identify themselves online for good.
What Are Biometrics?
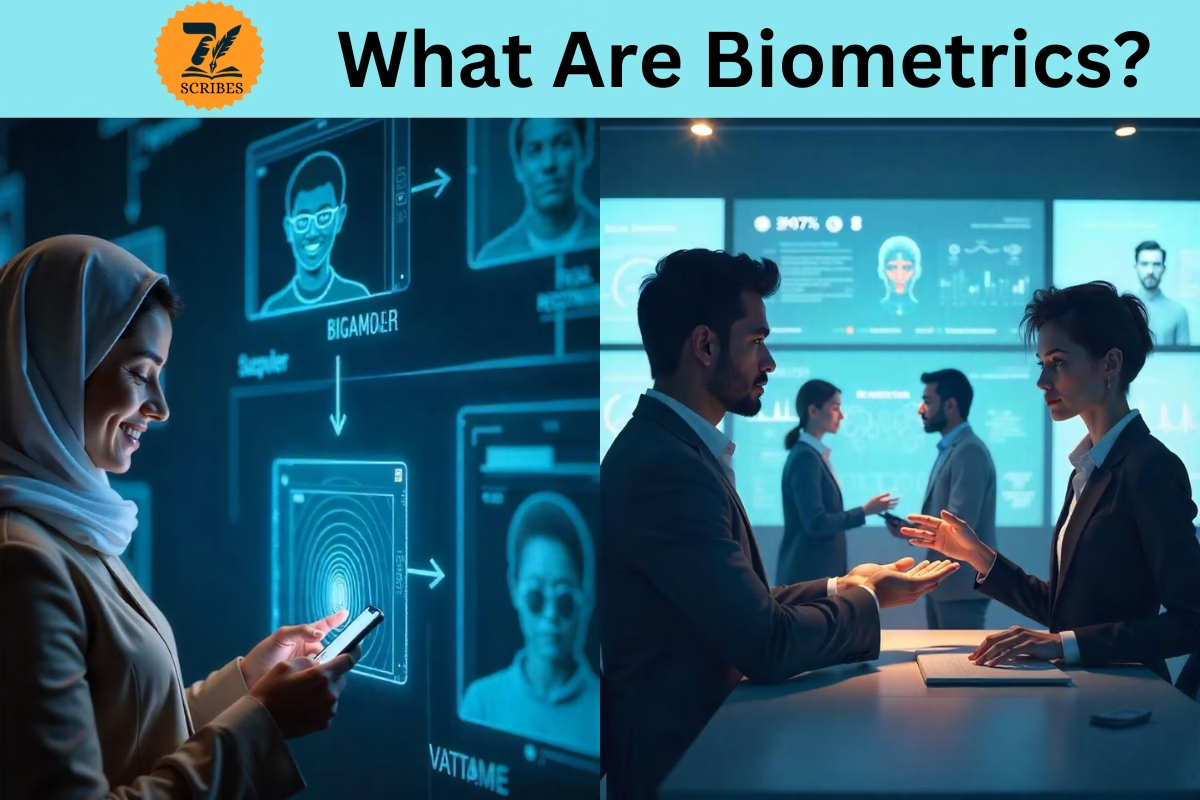
Biometrics means metrics and statistical analysis of unique physical or behavioral characteristics of individuals. Roughly speaking, this is the way to authenticate a person through the characteristics inherent in his or her body. These characteristics can be either ‘what we are’ like a finger, a face, or an eye (iris), or ‘what we do’ like walking or typing on a keyboard. The number of individuals with identical faces or with the same two fingers of the hand having the same fingerprint on them is nil, or in other words, it is precisely zero. This is what makes biometrics a great means of identification as it is much better than PINs and passwords which can be easily forgotten, stolen, or guessed.

Types of Biometrics
There are different biometric systems for identification based on different attributes and here are some of the most popular and more frequently used biometric identification methods:
Fingerprint Recognition
Fingerprint recognition is one of the most commonly used biometric verification methods and is gaining popularity each day. From unlocking phones to secure locations and even logging in to different applications, fingerprints have established themselves as a reliable and quick resource. Basically, due to its strength in uniqueness, it is not easy to overcome the system because no two people have similar fingerprints. With that uniqueness, this system is also said to have a good degree of security.
Facial Recognition
The use of smartphones forecasts well for the advancement and the use of facial recognition systems. This form of biometric security has become increasingly prevalent. Most people have probably utilized facial recognition technology to access their devices or to go through security checks at airports. Essentially, this system reconstructs the facial geometry using parameters like the distance between eyes, the structure of the cheekbone, the outline of the jaw, and other unique facial traits. With the rapid advancement of technology, this system has become so much more accurate that it only requires proper lighting to be effective.

Iris Scanning
The iris of an eye is a distinctively designed surface, rather like a fingerprint. It is known that iris scanning is one of the most secure biometric alternatives available. The technology employs infrared rays to take an in-depth photograph of a person’s iris for purposes of allowing access. However, iris recognition devices are utilized in airport facilities, government offices, and military bases, even though they are not as popular as facial recognition or fingerprint devices.
Voice Recognition
Voice recognition systems are gaining momentum in this day and age and gaining attention from people such as people who own virtual buyers of voice, e.g., Amazon Alexa, Google Assistant, and Apple Siri. The great voice recognition can also serve as the rubric to approve an individual for authentication. Every single person possesses a different voice, owing to the length of the vocal chords differentiates factors like pitch, speed, and tone, which together make a voice. Therefore, it is not surprising that the use of voice recognition is growing in the sphere of customer service, banking, and other secure communication systems.
Behavioral Biometrics
Just as it is well known that biometric identifiers are based on the physical characteristics of individuals, so too can one’s actions serve as the basis for such identifiers. For instance, how one types on a keyboard, the speed at which a person touches his phone, or how one walks, can also be reasonably identifiable. Although these sorts of behavioral biometrics are still in their infancy stage of development, they are very promising since they provide additional protection against fraudulent activities.
Why Biometrics?
Biometrics has started gaining grounds as authentication in the future and this could be the reason why:
- Stronger Security: The foremost benefit of using biometrics over any other authentication mechanisms is confidentiality and the level of security. Passwords and pins can be stolen, guessed, and cracked but features such as fingerprints and voices are not easily replicated. For instance, individuals are biographically authenticated for their face, thumbprints, and voice which makes it nearly impossible to lose that authentication which increases the risk of fraud significantly.
- Convenience: Passwords can be difficult to remember as dealing with security questions can be a tedious affair, in contrast, biometric authentication fosters ease of access as individuals would only need to be authenticated through their fingerprints, facial scans, or voice. Thus, making it easier to secure devices, accounts, and data without any hassle.
- Speed: The biggest advantage, no one likes waiting, especially when it comes to using electronic devices. Long passwords, tons of security questions, and verification codes make the process long and annoying. However, this will not be the case when using biometric scanners, whether it’s unlocking a phone or logging into an account, all it takes is a simple scan.
- Non-transferable: Biometric templates are nontransferable, unlike passwords which can be shared or even stolen. Furthermore, every person possesses their own unique set of looks or traits and characteristics therefore, impersonating anyone will be a difficult task.
Barriers To The Adoption Of Biometrics
Although biometrics can be quite interesting, there are some challenges to overcome. Like with anything new, certain obstacles need to be cleared before it is adopted by all spheres of life.
- Informed Consent: The matter of storing and dealing with biometric data poses a lot of ethical concerns. A biological part can be hard to change, and if it were to get breached, there would be a lot of implications if a breach ever took place. If a hacker has access to the information of a biometric database, they could potentially harm you and your identity, such scenarios can be worse than having a potential breach of password. So, making sure that there are certain measures such as security in place and a way of protecting oneself is vital for the smooth running of this technology.
- Bias in Data: The use of biometric systems that require equipment such as iris or CC cameras can be pricey which could there by use detrimental to the budget. This would not allow the systems to be well used across the globe, tiny organizations, or countries without sufficient resources.
Insights on Biometric Authentication
Even with these challenges, however, biometrics are rapidly taking over as they are the future and there are interesting prospects once the technology matures. The evolution of technology might bring us things like DNA biometrics or sensors that check heartbeats and body temperature for authentication soon.
With the implementation of biometric authentication systems in place, it would be easy to replace passwords as the only requirement to authenticate. Just like other biometric authentications, replacing passwords will make functions such as logging into devices, placing online purchases, and others much easier and more secure. Imagine coming to your home, car, or office and all you have to do is glance at the door and it unlocks itself! The potential this has with biometrics is unimaginable.
Furthermore, as more biometrics are implemented into businesses, the technology will be essential in combating fraud, protecting private information, and in the medical field such as ensuring proper identification of patients and medical professionals to minimize errors while achieving maximum safety.
Read more
The Evolution of Nanotechnology: A Fascinating Journey Through Science and Innovation
From Bitcoin to Blockchain: The Evolution of Cryptocurrencies
From Sensors to Society: The Evolution of the Internet of Things